













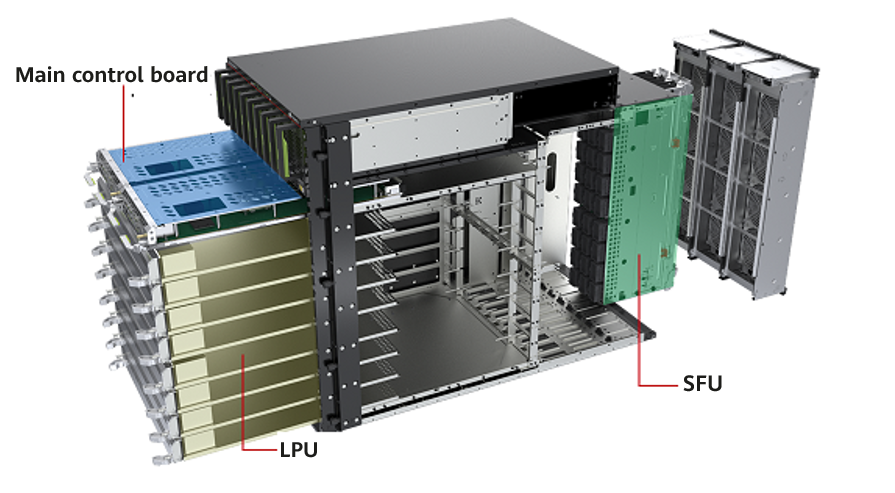















Within hours of its public release, the offensive security framework Hexstrike-AI has been weaponised by threat actors to exploit zero-day vulnerabilities, most recently affecting Citrix NetScaler ADC and Gateway, within just ten minutes.
Hexstrike-AI links large language models like Claude, GPT and Copilot via a Multi-Agent Control Protocol (MCP) to over 150 security tools.
Automated agents execute actions such as scanning, exploiting CVEs and deploying webshells, all orchestrated through high-level commands like 'exploit NetScaler'.
Researchers from CheckPoint note that attackers are now using Hexstrike-AI to achieve unauthenticated remote code execution automatically.
The AI framework's design, complete with retry logic and resilience, makes chaining reconnaissance, exploitation and persistence seamless and more effective.
 Hot Tags :
Artificial Intelligence
Critical infrastructure
Cyber norms
Hot Tags :
Artificial Intelligence
Critical infrastructure
Cyber norms