






















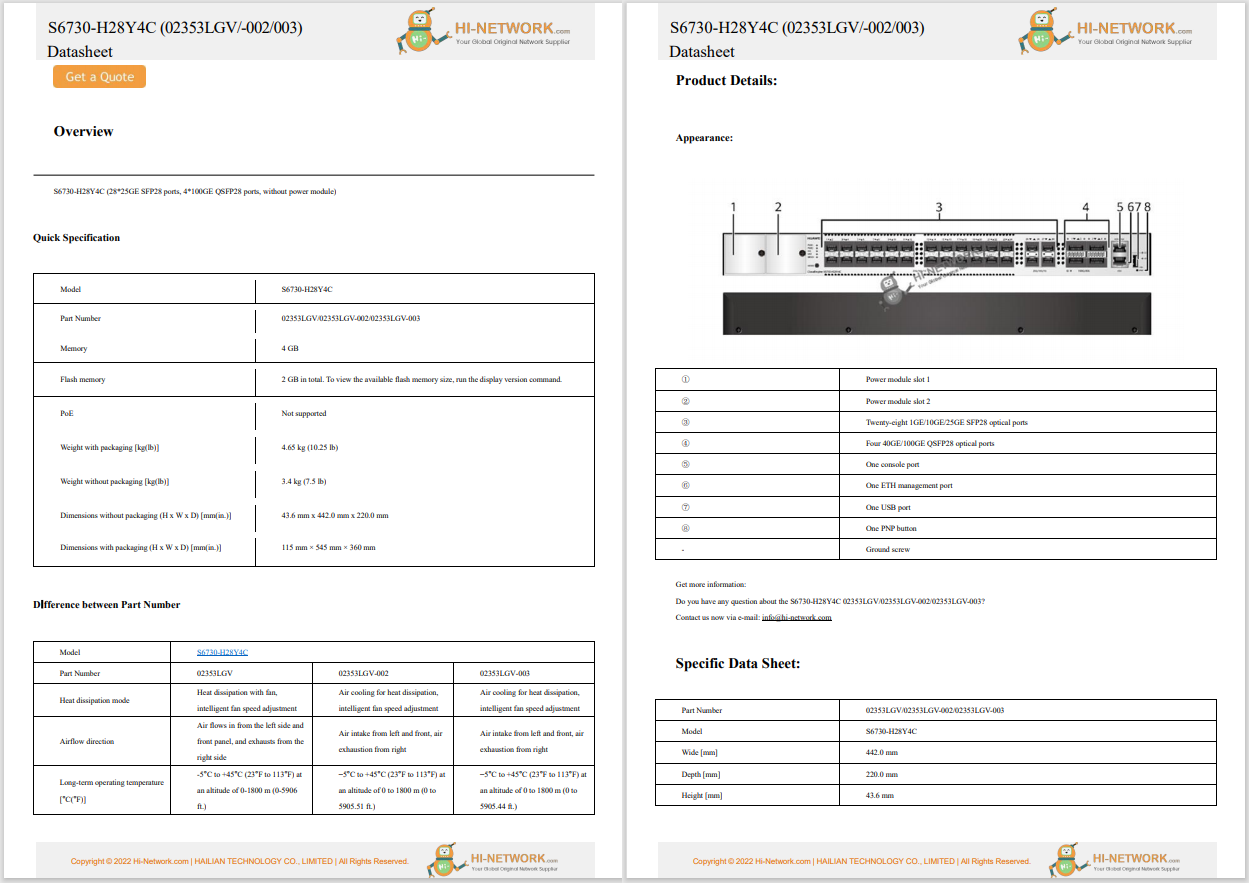


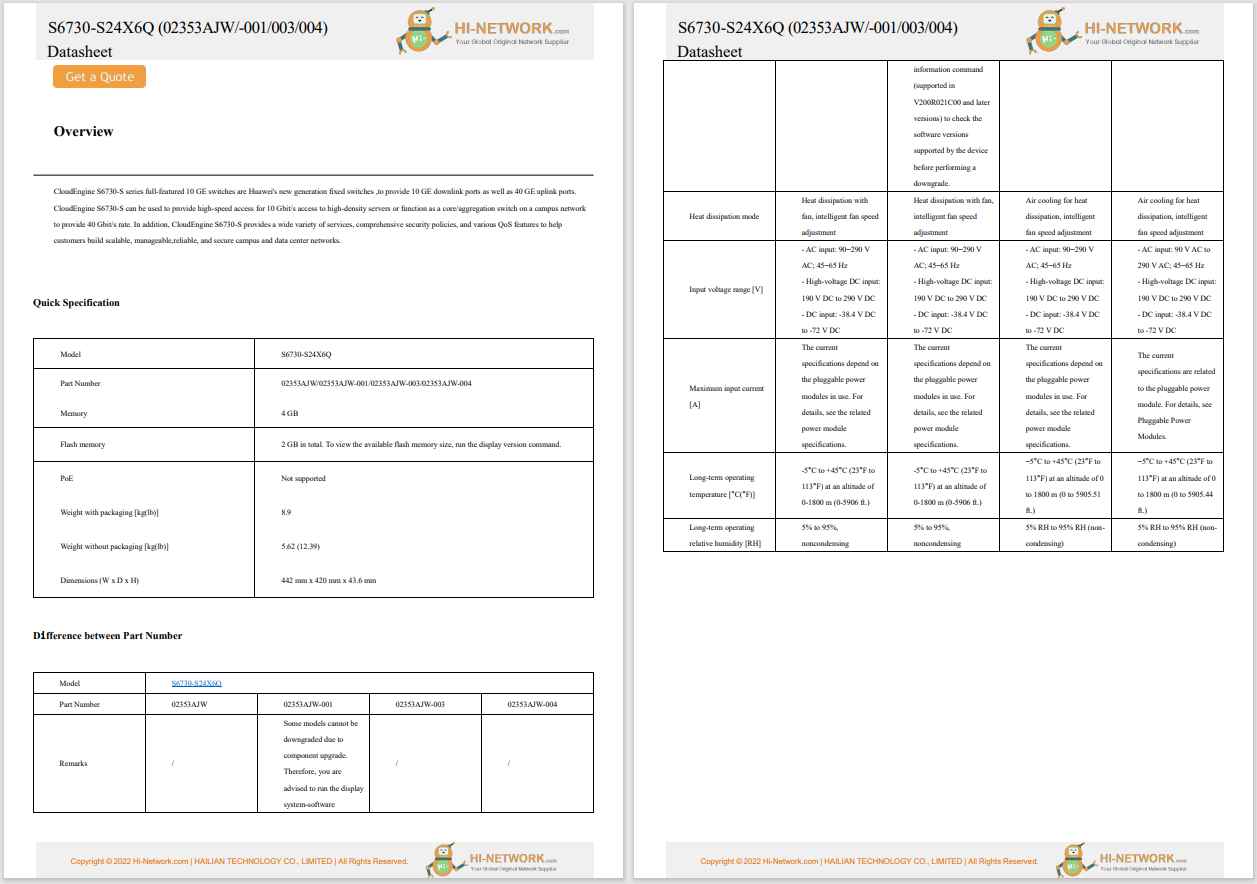
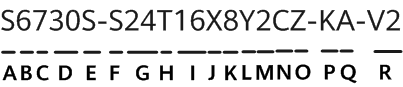
CISA is urging users of Zoho's ManageEngine ADSelfService Plus to update their tools, noting that APT actors are actively exploiting a recently discovered vulnerability.
Zoho ManageEngine ADSelfService Plus build 6114, which Zoho released on September 6, 2021, fixes the vulnerability.
ManageEngine ADSelfService Plus is a widely used self-service password management and single sign-on solution. The critical authentication bypass vulnerability affects representational state transfer (REST) application programming interface (API) URLs that could enable remote code execution.
In a joint advisory sent out this week, CISA, the FBI and the US Coast Guard Cyber Command said APT actors have already targeted "academic institutions, defense contractors and critical infrastructure entities in multiple industry sectors -- including transportation, IT, manufacturing, communications, logistics, and finance."
According to CISA, cybercriminals and nation-states exploiting the vulnerability are able to upload a .zip file containing a JavaServer Pages (JSP) web shell masquerading as an x509 certificate: service.cer. From there, more requests are made to different API endpoints to further exploit the victim's system, according to the advisory.
"After the initial exploitation, the JSP web shell is accessible at /help/admin-guide/Reports/ReportGenerate.jsp. The attacker then attempts to move laterally using Windows Management Instrumentation (WMI), gain access to a domain controller, dump NTDS.dit and SECURITY/SYSTEM registry hives, and then, from there, continues the compromised access. Confirming a successful compromise of ManageEngine ADSelfService Plus may be difficult -- the attackers run clean-up scripts designed to remove traces of the initial point of compromise and hide any relationship between the exploitation of the vulnerability and the web shell," CISA explained.
"Illicitly obtained access and information may disrupt company operations and subvert US research in multiple sectors. Successful exploitation of the vulnerability allows an attacker to place web shells, which enable the adversary to conduct post-exploitation activities, such as compromising administrator credentials, conducting lateral movement, and exfiltrating registry hives and Active Directory files."
CISA added that organizations need to ensure that ADSelfService is not directly accessible from the internet and the recommended "domain-wide password resets and double Kerberos Ticket Granting Ticket (TGT) password resets if any indication is found that the NTDS.dit file was compromised."
Threat actors have been exploiting the vulnerability since August, and CISA said they had seen a variety of tactics used to take advantage of the flaw, including frequently writing web shells to disk for initial persistence, obfuscating files or information, conducting further operations to dump user credentials and more.
Others have used it to add or delete user accounts, steal copies of the Active Directory database, delete files to remove indicators from the host and use Windows utilities to collect and archive files for exfiltration.
The situation is so serious that the FBI said it is "leveraging specially trained cyber squads in each of its 56 field offices and CyWatch, the FBI's 24/7 operations center and watch floor, which provides around-the-clock support to track incidents and communicate with field offices across the country and partner agencies."
CISA is also offering affected organizations help, and the US Coast Guard Cyber Command said it is providing specific cyber coverage for marine transportation system critical infrastructure.
Oliver Tavakoli, CTO at Vectra, toldZDNetthat finding a critical vulnerability in the system intended to help employees manage and reset their passwords "is exactly as bad as it sounds."
Even if the ADSelfService Plus server were not accessible from the internet, it would be accessible from any compromised laptop, Tavakoli noted.
He added that recovering from an attack will be expensive because "domain-wide password resets and double Kerberos Ticket Granting Ticket (TGT) password resets" are disruptive by themselves. The APT groups may have established other means of persistence in the intervening time, he noted.
BreachQuest CTO Jake Williams said it was important that organizations note the frequent use of web shells as a post-exploitation payload.
"In this case, threat actors have been observed using web shells that were disguised as certificates. This sort of activity should stand out in web server logs - but only if organizations have a plan for detection," Williams said.
"Given that this will certainly not be the last vulnerability that results in web shell deployment, organizations are advised to baseline normal behavior in their web server logs so they can quickly discover when a web shell has been deployed."
Like Digital Shadows senior cyber threat intel analyst Sean Nikkel, other experts explained that this issue is the fifth instance of similar, critical vulnerabilities from ManageEngine this year.
These vulnerabilities are severe in that they allow either remote code execution or the ability to bypass security controls, Nikkel told ZDNet.
"Since the service interacts with Active Directory, giving attackers access can only lead to bad things, such as controlling domain controllers or other services. Attackers can then take advantage of 'blending in with the noise' of everyday system activity. It's reasonable to assume that there will be more widespread exploitation of this and previous vulnerabilities given the interactivity with Microsoft system processes," he said.
"The observation that APT groups are actively exploiting CVE-2021-40539 should highlight the potential exposure it might cause. If trends are consistent, extortion groups will likely seek exploitation for ransomware activity in the not-so-distant future. Users of Zoho's software should apply patches immediately to avoid the types of compromise described in the CISA bulletin."
The vulnerability is part of a larger trend of issues being found with systems management software tools. Vulcan Cyber CEO Yaniv Bar-Dayan compared it to recent issues with SolarWinds, Open Management Infrastructure (OMI), Salt and more.
"Considering the amount of access and control these tools have, it is critical IT security teams take immediate steps to remediate fully. Zoho has a patch, but it is just a patch for one vulnerable component of what is a multi-layered, advanced persistent threat," Yaniv Bar-Dayan added.
"Apply the patch, but also make sure to eliminate direct access to ManageEngine software from the Internet where possible. If APT groups get access to systems management tools, they get the keys to the kingdom. Move quickly."
 Hot Tags :
Tech
Security
Hot Tags :
Tech
Security