






















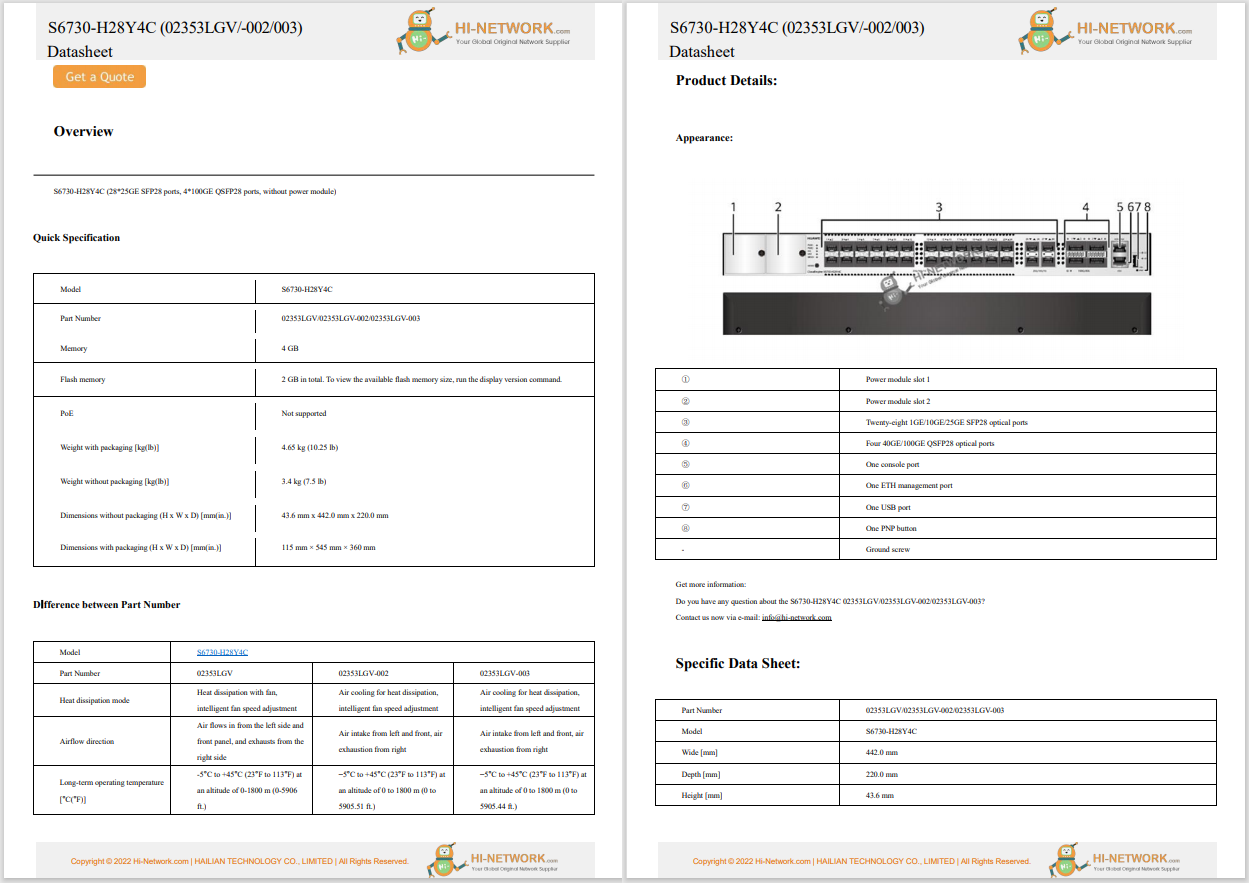


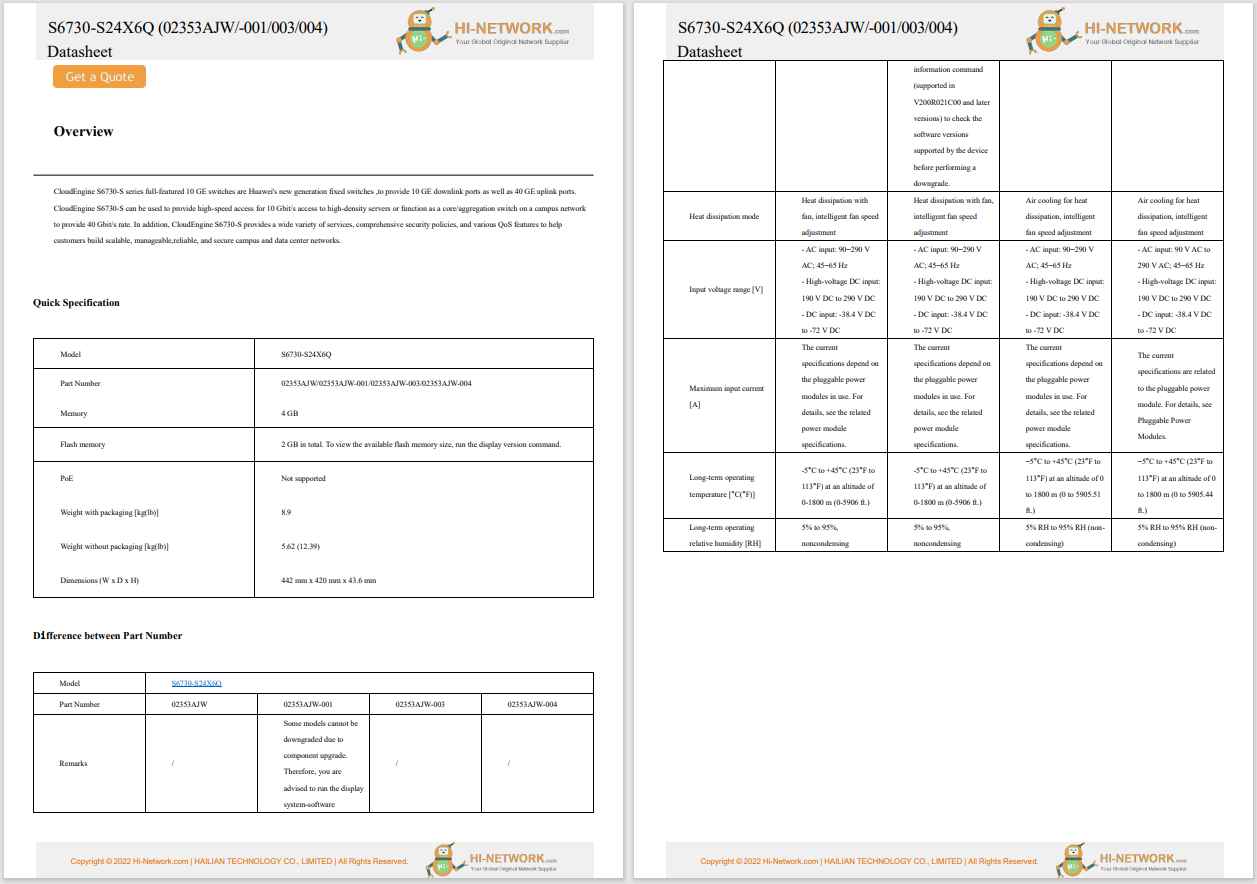
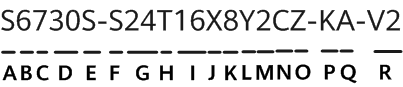

According to Tan Sri Richard Malanjum, Malaysia's chief justice,judges in the country will soon begin using artificial intelligence (AI) to help them issue more consistent decisions. A data-driven tool named 'data sentencing' is c...

Researchers fromOnline safety company AntiToxin Technologies, during an investigation commissioned by T.echCrunch, has found that Microsoft's Bing search engine shows child pornography images as well as provides suggestions for ot...

After the first KSK rollover in October 2018, ICANN has finished the process and revoked the old 2010 key from the root zone.The KSK helps protect the domain name system (DNS) and overall Internet security. This change was essenti...

Regulators are preparing to fix the rates drivers for ride-hailing services receive, after drivers demands for more oversight and higher rates, as reported byReuters. As part of an attempt to expand sharing economy services in Sou...

Upon receiving requests from many members of parliament to amend the draft law, the Tunisian Ministry of Interior withdrew the biometrics identification bill from the Assembly of the Representatives of the People. Since ...

Indonesia's Ministry of Communication and Information Technology haslaunched a web crawler -'Cyber Drone 9' -to identify, and prevent access to, offensive online content. The crawler is an automated software, powered by machine le...

Researchers from several corporate and university centres have revealed critical vulnerabilities in the processor chips made by lead vendors, such as Intel, AMD, ARM and Qualcomm. The two exploits of these vulnerabilities, present...

Uber and the Roads and Transportation Authority (RTA) in the Emirate of Dubai have signed anagreement under which Uber becomes fully regulated by the RTA. According to the agreement, Uber will be able to use 14,000 vehicles ...

World Economic Forum "Global Risks Report 2017" identified rising cyber dependency among top 5 trends that determine global developments. The report also labeled massive incident of data fraud/theft and large-scale cyberattacks ar...

The European Telecommunications Standards Institutehas launched an Industry Specification Group on cross-sector Context Information Management (ISG CIM) for smart cities applications and beyond. The group will work on developing s...

Google launched the beta version of its Cloud Key Management Service (KMS), which enables admins to manage their encryption keys in a cloud-hosted solution without maintaining an on-premise management system. Amazon Web Services (...

ICANN published theresults of its annual survey measuring the satisfaction of IANA functions customers regarding the services they receive. In particular, the survey measures satisfaction in relation to documentation quality, proc...