


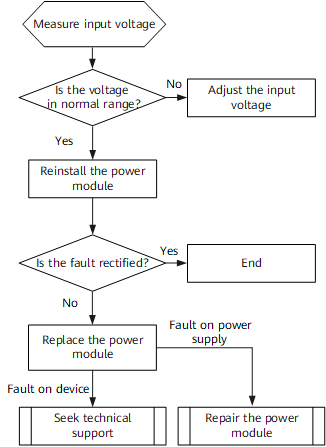

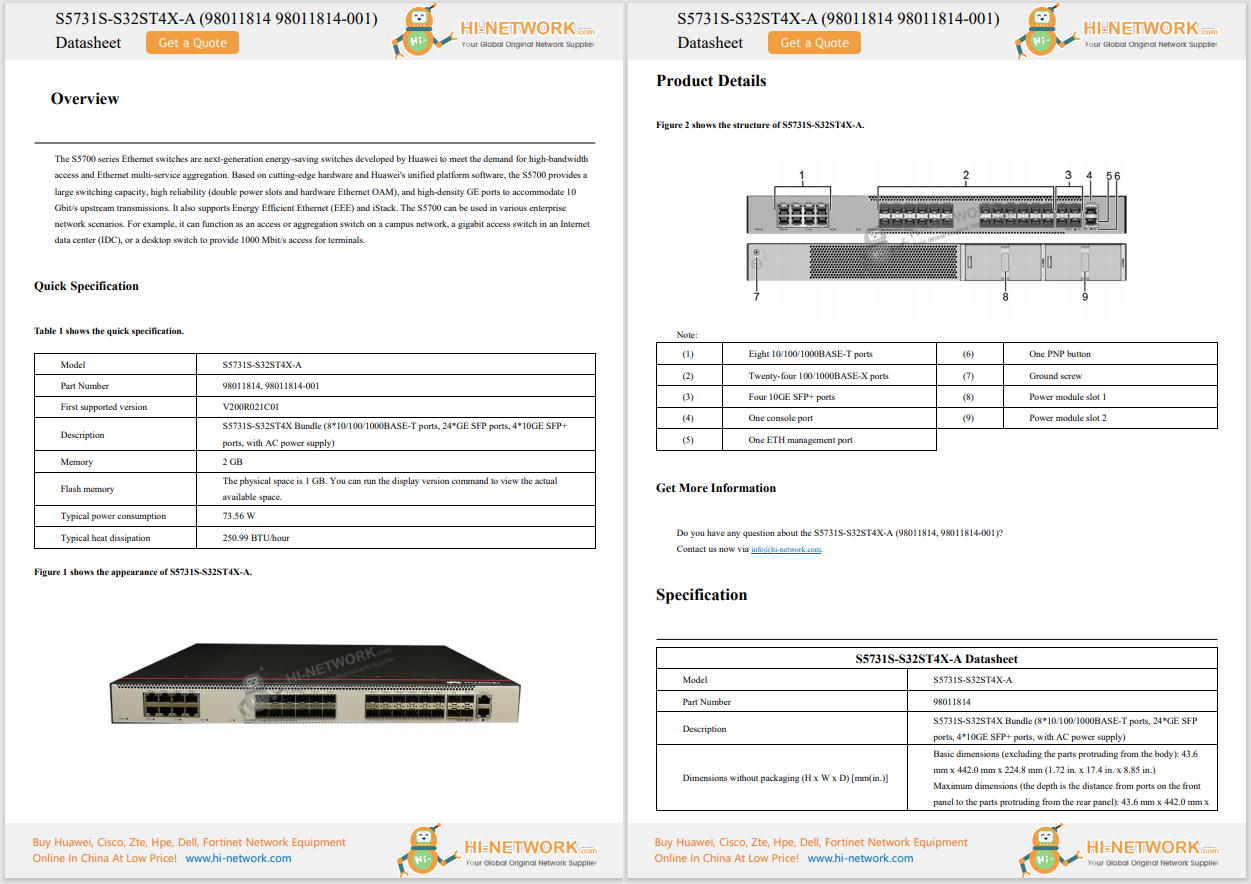











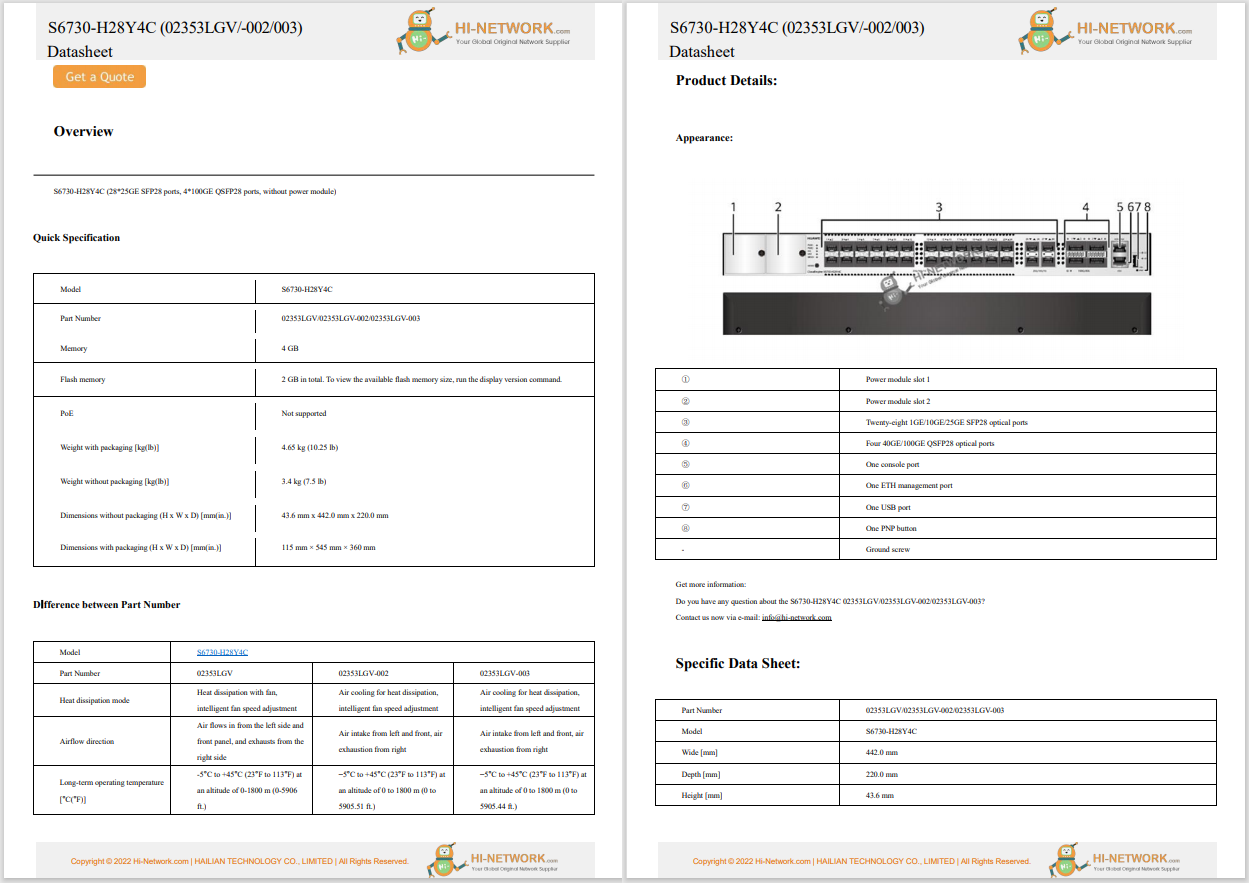










Shaping New Tax Services with Digital Technologies

Huawei Smart Customs Solution: Making Cross-Border Trade Easier and Secured Mar 25, 2021 [Shenzhen, China, March 25, 2021] Huawei launched the Smart Customs Solution globally during the Huawei Industrial Digital Tr...

Huawei: Explore the HEIGHT of the Intelligent World, Using Intelligent Twins as the Reference Architecture

Huawei Proposes Optical Slicing as the Cornerstone for Next-Generation Optical Transport Networks Mar 25, 2021 [Shenzhen, China, March 25, 2021] Richard Jin, President of Huawei's Transmission and Access Product Li...

Huawei Launches the Smart Classroom Solution

Throughout 2021, Cisco Financial Services will continue to examine how 'Connect, Secure, and Automate' -our strategy for helping customers accelerate their digital agility -enables financial institutions to deliver digital-first c...

Welcome to my first blog as leader of the new Partner Managed and as-a-Service team! I have had the pleasure of working with many of you in our partner community over the years. My team is focused on improving the end-to-end engag...

Meraki|has|more than 300 API requests in its arsenal. That means network engineers, software developers, and essentially anyone interested in automating their networks have the best and the most useful APIs ready for use. And all ...

Recently, I weighed in on what I see as a critical choice for higher education. Either, universities can slowly abandon hybrid learning as the threat of COVID-19 wanes, or dou...

Cisco is driving innovation to take a significant leap forward in hybrid cloud automation today, by bringing the benefits of infrastructure as code (IaC) automation to hybrid cloud environments. We are delighted to announce t...

Cisco and NetApp have been partnering to create trusted and versatile FlexPod converged infrastructure for more than a decade now. Many of our close to 10,000 customers continue to tell us that FlexPod is ideal for applications wi...

Network telemetry is a reservoir of data that, if tapped, can shed light on users' behavioral patterns, weak spots in security, potentially malicious tools installed in enterprise environments, and even malware itself. Global thre...